Vallhalloween - Forensics (Windows Event Logs)

Summary
Vallhalloween is a medium difficulty challenge from HacktheBox’s “HacktheBoo 2023” CTF Event. It involves reading several Windows event logs to find the infection path of a ransomware incident.
Challenge Description
Event Log Analysis
First. we download the given logs & connect to the docker instance using ncat. To solve this challenge, I used a Windows10 virtual machine to easily read the Event Logs (although there are Linux tools for this as well). When we connect to the docker instance, we receive a series of prompts and a description:
+--------------+--------------------------------------------------------------------------------------+
| Title | Description |
+--------------+--------------------------------------------------------------------------------------+
| Valhalloween | As I was walking the neighbor's streets for some Trick-or-Treat, |
| | a strange man approached me, saying he was dressed as "The God of Mischief!". |
| | He handed me some candy and disappeared. Among the candy bars was a USB in disguise, |
| | and when I plugged it into my computer, all my files were corrupted! |
| | First, spawn the haunted Docker instance and connect to it! |
| | Dig through the horrors that lie in the given Logs |
| | and answer whatever questions are asked of you! |
+--------------+--------------------------------------------------------------------------------------+The first question asks us the IP and port of the server where the malware was downloaded. Often, malware is downloaded through a malicious PowerShell process. To find this, we can search the PowerShell event logs for any HTTP requests:
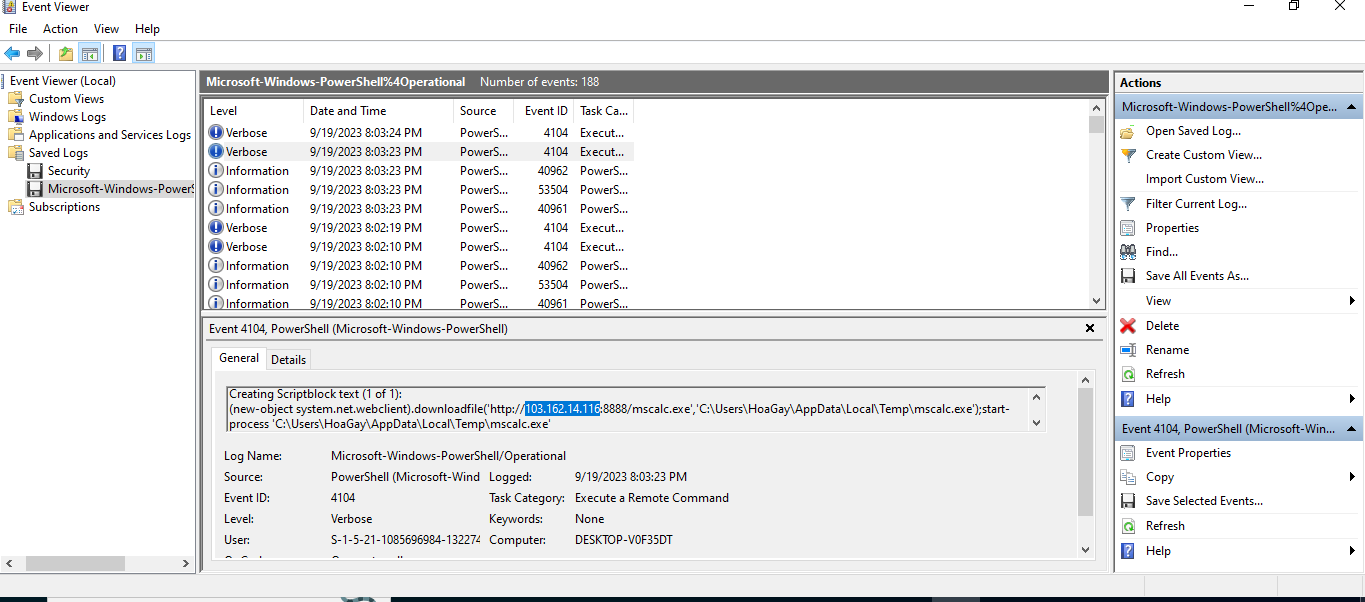
We submit this IP and port on to the prompt on our ncat connection to verify that it is correct:
←[95mWhat are the IP address and port of the server from which the malicious actors downloaded the ransomware? (for example: 98.76.54.32:443)
←[0m> 103.162.14.116:8888
←[92m[+] Correct!The next prompt requires us to find the MD5 hash in the sysmon logs. So, we open the log in event viewer and look for the MD5 hash:
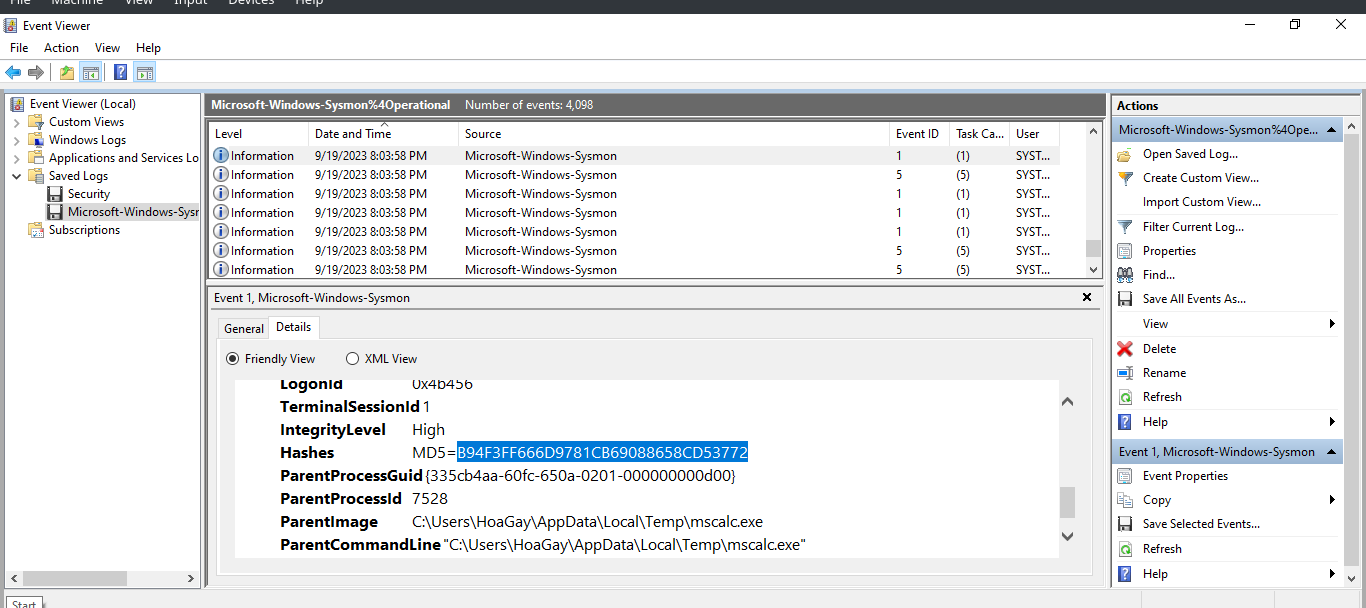
←[95mAccording to the sysmon logs, what is the MD5 hash of the ransomware? (for example: 6ab0e507bcc2fad463959aa8be2d782f)
Please wait 1 seconds..nds.
> B94F3FF666D9781CB69088658CD53772
←[92m[+] Correct!Next, we are asked to research if this is a known type of malware by searching the hash on a service like VirusTotal
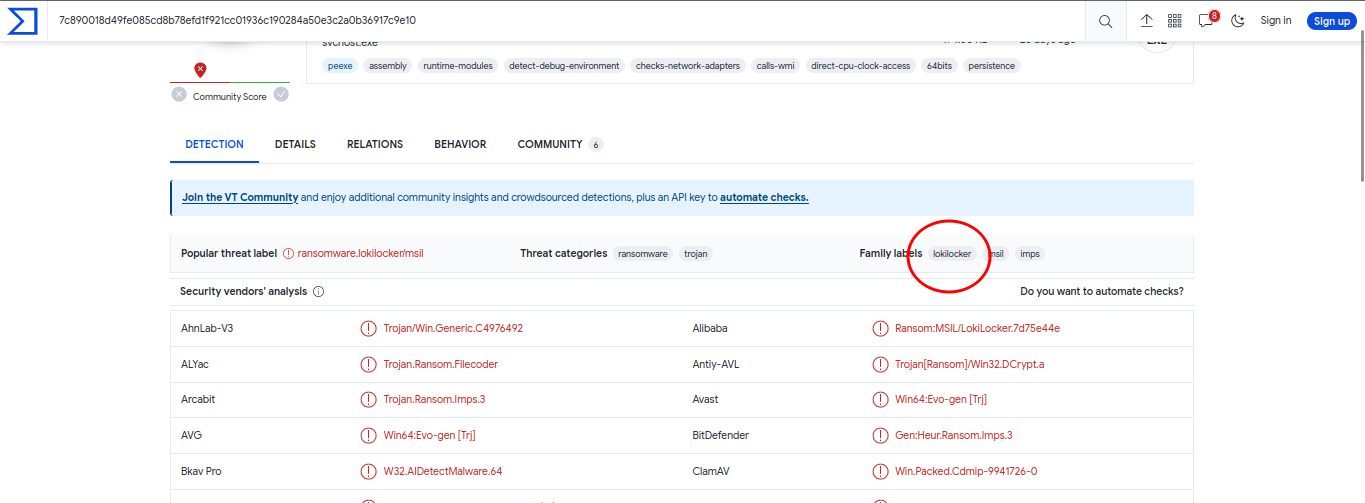
←[95m←[95mBased on the hash found, determine the family label of the ransomware in the wild from online reports such as Virus Total, Hybrid Analysis, etc. (for example: wannacry)
←[0m> lokilocker
←[92m[+] Correct!Next, we are tasked with identifying the scheduled task created by the malware. For this, we open the Task Scheduler log and look for tasks created around the time the malware was downloaded. We find a task “Loki” that was created:
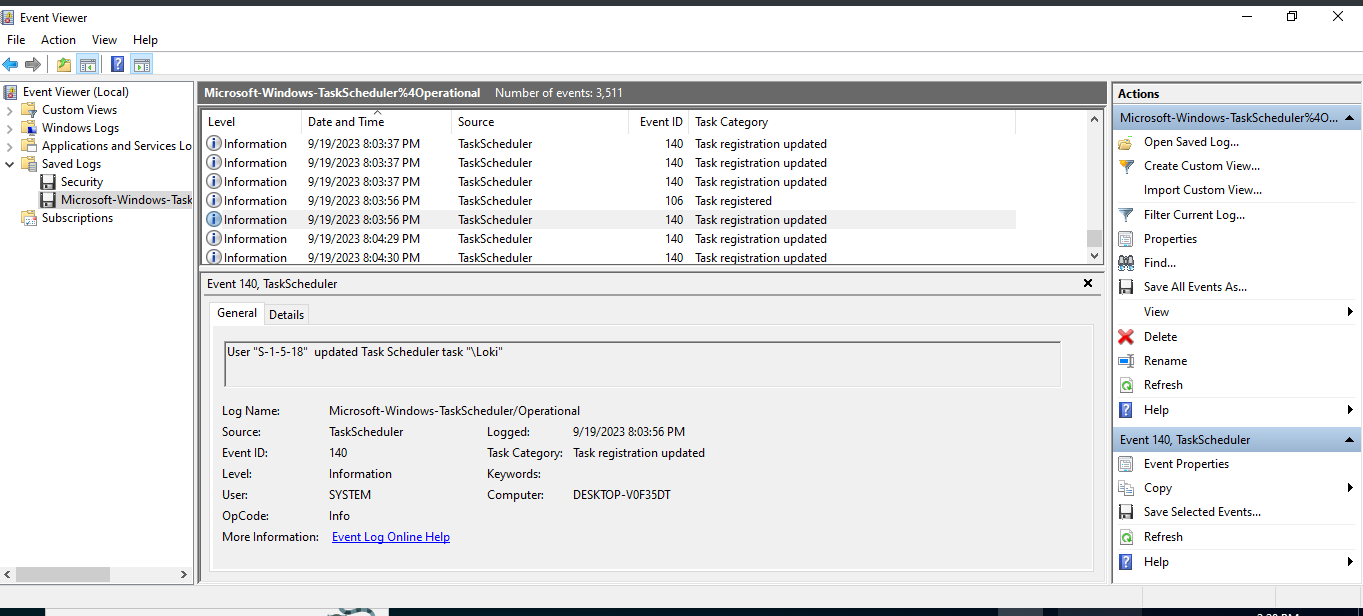
←[95mWhat is the name of the task scheduled by the ransomware? (for example: WindowsUpdater)
Please wait 1 seconds..nds.
> Loki
←[92m[+] Correct!We are asked for the parent process name and ID of the ransomware. We know that the malware was downloaded over PowerShell, so we look for a PowerShell process around the time of infection.We can find this in the sysmon logs as well.
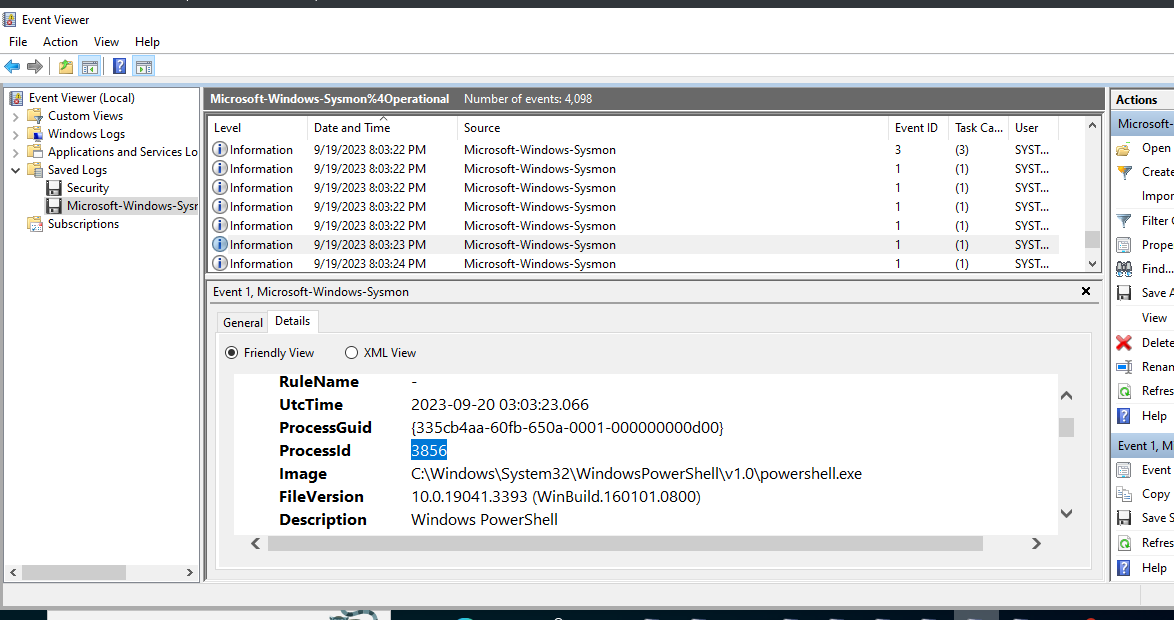
←[95mWhat are the parent process name and ID of the ransomware process? (for example: svchost.exe_4953)
←[0m
> powershell.exe_3856
←[92m[+] Correct!Ideally, we will want to know the initial attack vector and not just the information gathered so far.
Upon further inspection of the sysmon log, we find that the infection was caused by a malicious .docx file:
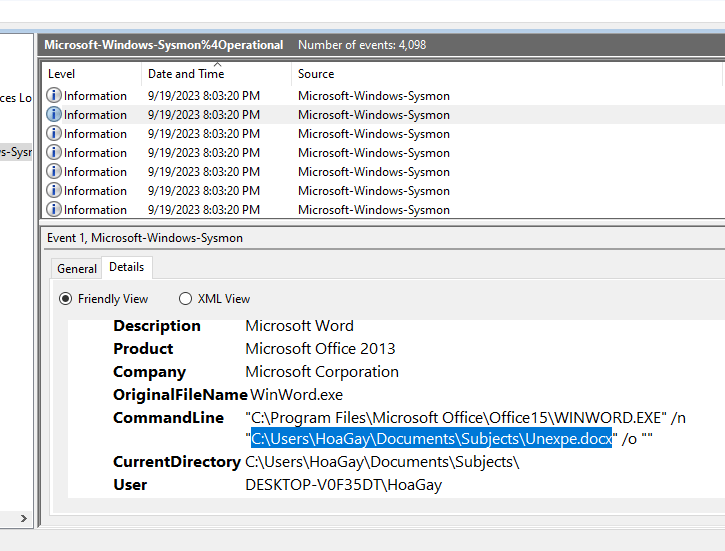
←[95m←[95mFollowing the PPID, provide the file path of the initial stage in the infection chain. (for example: D:\Data\KCorp\FirstStage.pdf)
←[0m> C:\Users\HoaGay\Documents\Subjects\Unexpe.docx
←[92m[+] Correct!We also want to know what time the infection began, so we search the logs for when this file was opened:
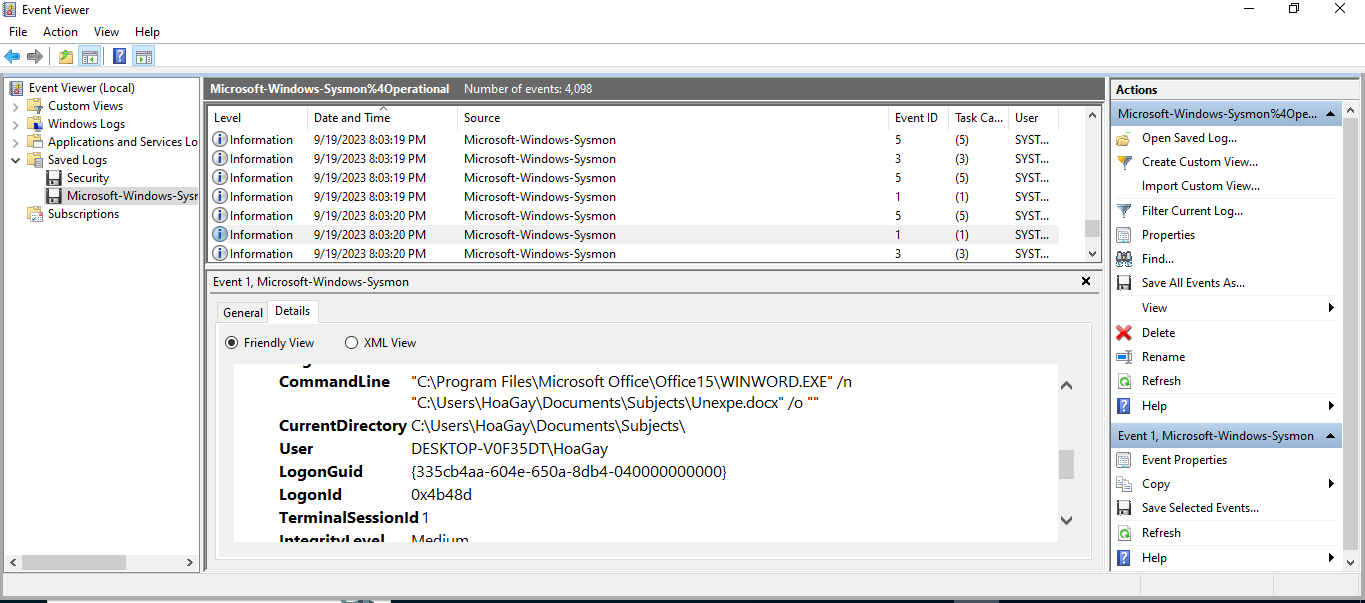
←[95mWhen was the first file in the infection chain opened (in UTC)? (for example: 1975-04-30_12:34:56)
←[0m
> 2023-09-20_03:03:20
←[92m[+] Correct!At this point, you should receive the flag from the program that you are connected to over ncat.
Conclusion
Throughout this challenge, we are asked a series of guiding questions in our analysis of Windows Event logs during a ransomware incident. We determined that the initial infection vector was the opening of a malicious Word document which resulted in the lokilocker infection.
